Secure your servers from POODLE (SSLv3) attacks
I guess you all heard of the recent SSLv3 vulnerability or POODLE a couple days ago. It is a protocol flaw issue so It will affects every implementation of SSLv3. To understand more about this exploit, please read:
There are already a lot of instructions on how to harden your servers and clients to prevent this kind of attack available on the Internet. Here is a short one I'm using for my servers:
1. nginx:
* Create a configuration for ssl /etc/nginx/conf.d/strong-ssl.conf with the following content (disable SSLv3 and use strong ciphers):
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS";
* Restart nginx:
$ sudo service nginx restart
2. apache:
* Disable SSLv3 by modify this file /etc/apache2/mods_available/ssl.conf:
...
SSLProtocol all -SSLv3 -SSLv2
...
* Restart apache:
$ sudo service apache2 restart
In addition, you can check your servers (and clients) SSL security using this website:
https://www.ssllabs.com/ssltest/
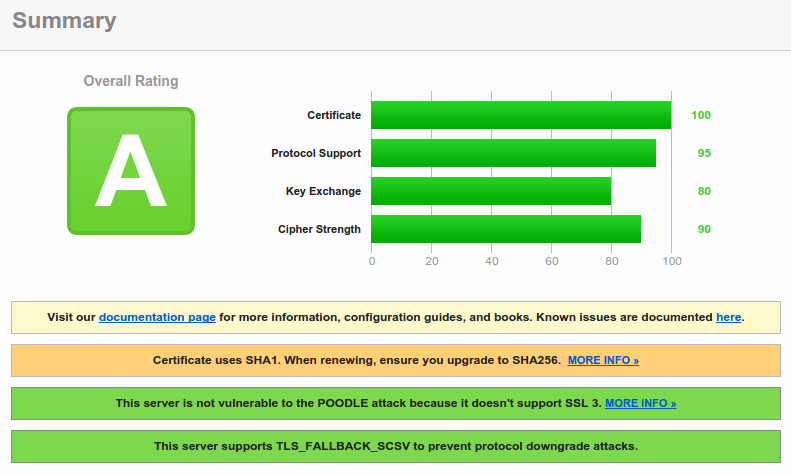
If the result is something like this, you should be OK:
- White paper: https://www.openssl.org/~bodo/ssl-poodle.pdf
- StackExchange discussions: http://security.stackexchange.com/questions/70719/ssl3-poodle-vulnerability
There are already a lot of instructions on how to harden your servers and clients to prevent this kind of attack available on the Internet. Here is a short one I'm using for my servers:
1. nginx:
* Create a configuration for ssl /etc/nginx/conf.d/strong-ssl.conf with the following content (disable SSLv3 and use strong ciphers):
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS";
* Restart nginx:
$ sudo service nginx restart
2. apache:
* Disable SSLv3 by modify this file /etc/apache2/mods_available/ssl.conf:
...
SSLProtocol all -SSLv3 -SSLv2
...
* Restart apache:
$ sudo service apache2 restart
In addition, you can check your servers (and clients) SSL security using this website:
https://www.ssllabs.com/ssltest/
If the result is something like this, you should be OK:
Comments
Post a Comment